Dear insurance industry, it's time to have a chat.
On boxing day, Financial Times released an article where Mario Greco, the Zurich Insurance CEO stated “What will become uninsurable is going to be cyber,” and “What if someone takes control of vital parts of our infrastructure, the consequences of that?” .
This of course lead to groups of people from both sides of the “insurable/non-insurable” argument to come out with their own spins and comments on the words of Greco.
For a while I’ve been observing the different parties that play a role in cyber insurance and seeing posts and comments from all sides that are just incorrect or misinformed. I decided to write this post as an attempt to have an honest talk about cyber insurance as an industry, and fixing some of the narrative that is currently on-going, for us to move on and build a better industry for all parties involved.
Our main parties for this blogpost are: Policyholders, Brokers, Insurance providers (insurance/mga), Re-insurance companies, Information Security organizations and professionals.
Policyholders
While the most important player (as they are the customer, and the customer should almost always be the most important), they are also the one with the easiest problem to solve, because their desire is “How can I get my premium to a more acceptable level?” so, here is your cheatsheet, to get a more cost effective cyber insurance coverage:
1 - Take your remote management (and critical or typically vulnerable) services off from being directly exposed to the internet. That means your RDP, SMB, Hypervisors… etc. Put all of that behind a VPN or SASE solution. If we see it, attackers see it. We don’t want to see it.
2 - Take your web login forms for managed appliances, systems and administrator panels off the internet. That means your wordpress login, firewall login page, PHPMyadmin and CPanel. Put all of it behind a VPN/SASE or SSO type of solution. We don’t want to see it.
3 - MFA - Enforce MFA everywhere. Read my words again, enforce, not just enable, not enforce on some, enforce it everywhere. Make it so that it’s not push notification for some extra points.
4 - Backups - Daily/Weekly backups, with monthly (or at least quarterly) restoration tests. Backups must be offline (separate from your day to day operations) and encrypted.
5 - Move away from on-prem Exchange. O365, Gmail enterprise, but no on-prem Exchange. It’s incredibly hard (some would argue impossible) to maintain a secure Exchange installation these days. It will get hammered even further in 2023.
These for steps will usually get your to a good security position and largely should get you a really acceptable coverage/premium balance if you use a modern insurance provider. If you want a few extra brownie points, have a strong control on transfers above a certain threshold to help with those pesky FTF attacks.
Understand what type of policy you have and what it covers. You read in the news often that “cyber insurance claims aren’t being paid” but that is actually false and a misrepresentation by the media. You look at Zürich vs Mondelez, but it wasn’t a cyber insurance policy that they had, it was a property insurance policy. You look at the EMOI Services case, but it wasn’t cyber either. They filed it under their business owner insurance policy.
Demand more from your cyber insurance provider. There are amazing offers out there that can even help you save on your infosec/it budget.
You read about war exclusions, this is actually something all other insurance lines have done. What LLoyds did, was give more detailed definitions, to remove ambiguity about when and where exclusions will apply.
Brokers
Dear Brokers, you are one of the most critical parties. You are an advisor to your customers, a sherpa, a guide, the warden of their coverage.
Do not let your customers take the cheaper path. Because in the medium to long term, it’s a path full of pain. Just because a quote is the cheapest, it doesn’t mean it’s the right quote for your customer. Just because it’s the provider that pays the highest commission, doesn’t mean that extra 1% is going to be the right choice to keep your customer happy.
When a policyholder has a claim, we all suffer, we all lose. You can put a stop to it. When the insurance company is telling you that the customer MUST fix something before we can bind, it’s because we’ve seen hackers use that exact thing to break into companies. It’s not because we want to add extra friction to your business.
So please please please, get the customer to fix that security issues found in scans. It will save everyone a lot of pain.
You are the central party that coordinates everyone, make sure you’re adding the right domains on the application, that you’re giving us the right policyholder contact (for us to notify them of security issues) and overall enable everyone to be their best selves. We all want the same, a happy customer.
Insurance Providers
The days of the PDF are over. Embrace technology, embrace scanning and start building technology, threat intelligence and security teams under your organizations if you want to be succesfull at underwriting cyber.
Buying 3rd party reports won’t work (you’re only getting a snapshot in time, and these companies don’t really know where claims are coming from). A risk might look one way today, and change tomorrow if a new vulnerability is released and you need to be prepared to give guidance on how to mitigate. You need to have that knowledge in-house integrated into your insurance workflow.
While some have criticized outside in scans, the reality is, we see what a hacker sees, so it’s a great place to start. Perfect? no, but a strong foundation. Build it. Understand how to price a risk, impact of a vulnerability and crediting defensive controls. As your teams how they think about the following scenarios:
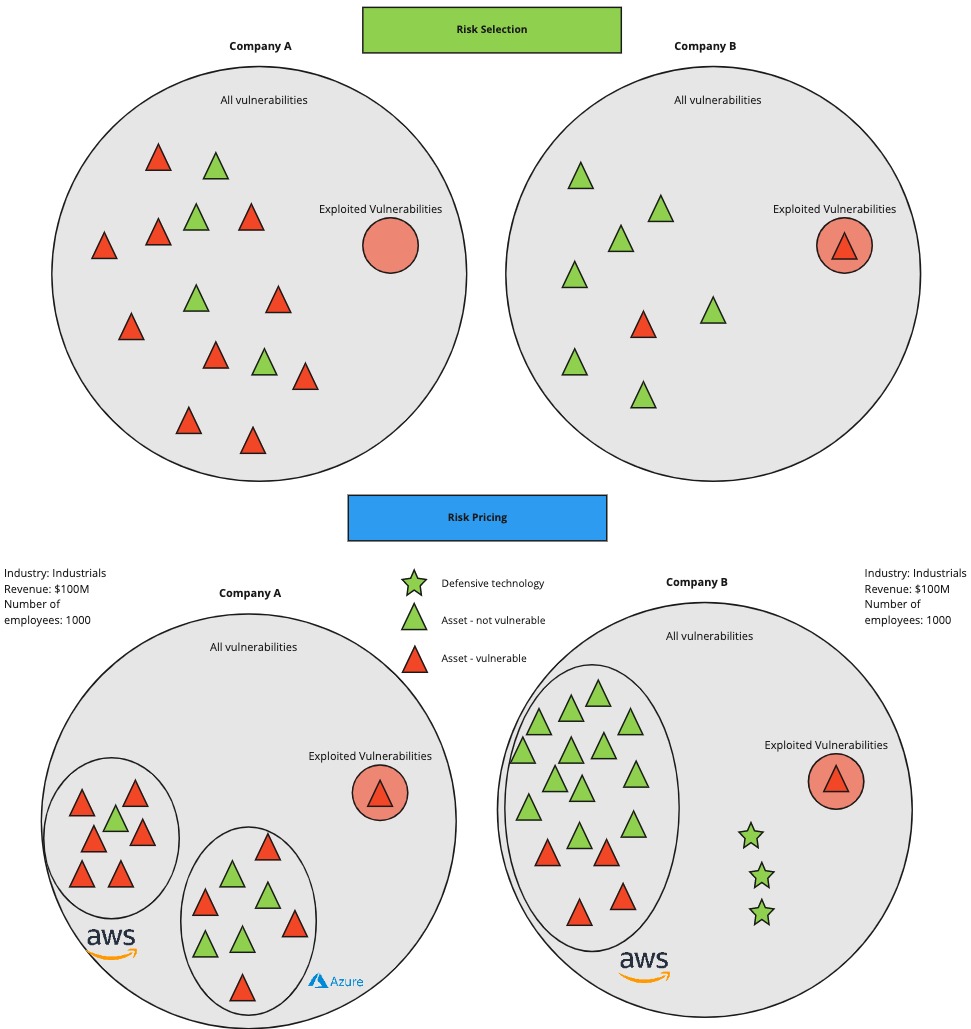
If the answer is “We look at industry and record count.” well… you have a problem.
Cyber is a line you will have to participate in the future, technology is all around, being a bigger and bigger part of our lives. AI, Cryptocurrencies, AR/VR, Metaverse, some of these might be fads, but they all play an important part in the discourse of our evolution as humanity, you need to understand which role they play and how they affect your coverage.
Move your way of thinking from “prevent the hack”, your policyholders will get hacked. Start asking them how they are going to contain the damage. and how fast they can recover after.
Move your mindset from just Prevention (as there are no silver bullets in cybersecurity) to Prevent, Contain, Restore.
Understand attacker behavior and which vulnerabilities matter.
Re-insurance companies
Cyber is a new type of risk. While a tendency to compare it to other lines or risks you already re-insure might be tempting, it just isn’t the same. You need to have a set of diversified skills just to understand the “cyber” part of the risk. From networking and cloud expertise, cybersecurity (web applications, network enabled services, mobile), to compliance, threat modelling and risk management.
The reality is that cyber is a risk that is very volatile and dynamic in it’s nature (new vulnerabilities being found on a daily basis and new software being built on a daily basis), but it’s one that still relies on humans to be exploited. Meaning that there is a limitation to the number of organizations that are being attacked at any time, and a limitation (based on incentives typically) on the vulnerabilities that will be and can be exploited at any time. I suggest you read on my previous blogpost on aggregation and why you need to be thinking at a more granular level.
You need to have technology experts that understand how the evolutions in technology are affecting your portfolio and also questioning your modelling. AWS isn’t a single blob that can go down for 30 days as some of the scenarios you’re presented by the modelling companies. AWS is a highly evolved cloud system with multi region, multi datacenter, highly redudant that sometimes has specific services and regions that go down.It’s also something so critical to the world, that if, for some un-godly (and physics law breaking) reason it did happen to go down for 30 days, it’s not a cyber insurance problem, it’s a government problem as you would struggle to get money out of your bank, food from the super market and many other bad things would happen (guess who would also live in this world? Attackers. Guess who doesn’t want this to happen to their families and themselves? Attackers.).
Yes the attack surface is expanding (which many use as an argument for cyber being uninsurable), but technology is also evolving and making good and reliable solutions available at more accessible prices for organisations. A few years ago you had no DDoS protection, now you can get Cloudflare for free.
Is there aggregation in cyber? Yes.
Is it as big as it’s currently being modelled ? No.
Your other risks tell you to look to historical events to model future events, but it’s very rare that a risk has a landscape change as cyber does.
Technology has evolved very fast, while a single individual was able with a home connection to DoS a major provider 10 years ago, today it would be a lot harder.
The cloud didn’t used to be multi region, multi data center and highly redudant, but today they are,and they hire the biggest experts in the world across all areas of technology to help keep those services alive and healthy.
EDRs and easier to use back up solutions didn’t use to be a thing. But today they are. MDR services are getting cheaper and more accessible, and organizations are starting to use them to leverage that expertise for security monitoring.
All of these evolutions, need to factor into your modelling, and they will continue to exist and evolve. With the advances in artificial intelligence, how soon until we have reliable AI agents defending networks, our policyholders, and portfolios? (my bet is next 3-5 years, and notice my use of the word reliable).
Be selective to whom you’re giving your re-insurance capacity. If you give it to insurance providers that don’t embrace technology (like scanning, continuous underwriting, pro-active security services and other techniques to help with risk mitigation, selection and reduction) you’re exacerbating the problem.
Have those companies that have access to technology about the insureds, help you get data to model your portfolio more accurately. You will be able to fix your reserving and help the market with capacity.
As you think about exclusions, first understand all of the above, then also ask cybersecurity experts how hard of a problema attribution is. An individual can buy or a hack a server in China/Russia, and then hack from that IP space, how will you distinguish what is war vs what isn’t? One hacking group can emulate and steal techniques from a government backed hacking group, how will we know who is who? Make it so that the organizations you’re covering are enforcing strong baselines on their policyholders, that way we improve security and recovery methods, so that even if one of these groups is successfull, the organization can get back online fast and have small/low impact.
The same applied to critical infrastructure. You have the power to move the needle on the security hygiene of those companies.
Information security organizations and individuals
I leave my favorites for last. I’ve been a part of this industry for a while now and seen different sides to it, from being a student, consultant and company founder, I’ve seen the good and the bad.
Embrace insurance. It’s a tool like any other and it’s in no way shape or form trying to replace security or it’s controls (It actually depends on your success.).
Learn how to talk and argue about risk in $ not CVSS scores. Your CFO doesn’t understand CVSS scores, nor should he. He wants to know how much insurance coverage he should buy to be comfortable with risk, and the brokers can be your friends here and help you out, the insurance providers give them tools to make this easy to explain!
There is going to be some hard times. Just because your company has a tool/technology that solves a problem, it doesn’t mean that problem is something being actively used.
I met with a (very big) security company a while ago that did a type of scanning that finds a specific set of vulnerabilities, and they were telling me about all the things they had discovered and asked me how soon I wanted to partner with them to reduce the amount of claims we were paying. The problem? In 3 years since I have been at Coalition there hasn’t been a single instance of us having a policyholder be compromised by that method.
While the security vulnerabilities were real, attackers simply don’t care, because they have other, simpler ways to get in.
Does that mean that in the future we won’t see this? No, but at least for now it’s not a priority problem for us, and if it isn’t for us, should it be for the companies trying to prioritize what they should fix when they have restricted budgets and limited security staff?
The insurance industry is going to play a critical part in your life. Take the time to understand it instead of just eating up what the media spouts. If you’re a startup, there are incredible opportunities for you to partner up with insurance companies, they need technical knowledge which you have, and you need exposure to companies security problems at large scale which they have.
Conclusion
Cyber is insurable. But we have a lot of work ahead of us.